README overhaul: embedded video, concise value prop, accurate security model, community tool gap
Showing
1 changed file
with
47 additions
and
97 deletions
| ... | @@ -10,54 +10,50 @@ | ... | @@ -10,54 +10,50 @@ |
| 10 | 10 | ||
| 11 | ## What It Is | 11 | ## What It Is |
| 12 | 12 | ||
| 13 | Moqui MCP puts AI directly into ERP systems - the software that runs every company on Earth. AI agents can now inhabit real corporate roles: purchasing, sales, HR, finance. | 13 | Moqui MCP puts AI into ERP systems - the software that runs every company. AI agents can now inhabit real corporate roles: purchasing, sales, HR, finance. |
| 14 | 14 | ||
| 15 | **Every product you touch passed through an inventory system. Now AI can touch it back.** | 15 | **Every product you touch passed through an inventory system. Now AI can touch it back.** |
| 16 | 16 | ||
| 17 | ## Why It Matters | 17 | ## Why It Matters |
| 18 | 18 | ||
| 19 | - **Real consequences**: Every action hits actual financials, inventory, supply chains | 19 | - **Real consequences**: Actions hit actual financials, inventory, supply chains |
| 20 | - **Real accountability**: P&L impact, compliance enforcement, audit trails | 20 | - **Real accountability**: P&L impact, compliance enforcement, audit trails |
| 21 | - **Real operations**: Not simulations - live business processes | 21 | - **Real operations**: Not simulations - live business processes |
| 22 | - **Real scale**: From corner stores to global supply chains | 22 | - **Real scale**: From corner stores to global supply chains |
| 23 | 23 | ||
| 24 | This is the foundation for autonomous business operations (ECA/SECA systems). | 24 | Foundation for autonomous business operations (ECA/SECA systems). |
| 25 | 25 | ||
| 26 | --- | 26 | --- |
| 27 | 27 | ||
| 28 | **⚠️ REQUIRES CONTAINERS & SECURITY ⚠️** | 28 | ### 💬 **From the Maintainer** |
| 29 | 29 | ||
| 30 | ## 🚨 SECURITY WARNING 🚨 | 30 | [](https://github.com/schue) |
| 31 | 31 | ||
| 32 | **NEVER deploy this with ADMIN access in production environments!** An LLM with ADMIN access can: | 32 | > *"Cut the junk. Ideas for JobSandbox integration?"* |
| 33 | 33 | ||
| 34 | - **Execute ANY Moqui service** - including data deletion, user management, system configuration | 34 | **Your input shapes the roadmap.** |
| 35 | - **Access ALL entities** - complete read/write access to every table in your database | ||
| 36 | - **Render ANY screen** - bypass UI controls and access system internals directly | ||
| 37 | - **Modify user permissions** - escalate privileges, create admin accounts | ||
| 38 | - **Delete or corrupt data** - mass operations, database cleanup, etc. | ||
| 39 | - **Access financial data** - orders, payments, customer information, pricing | ||
| 40 | - **Bypass business rules** - direct service calls skip validation logic | ||
| 41 | 35 | ||
| 42 | ## 🛡️ SAFE USAGE REQUIREMENTS | 36 | --- |
| 37 | |||
| 38 | **⚠️ CONTAINERS & SECURITY REQUIRED ⚠️** | ||
| 39 | |||
| 40 | ## 🛡️ **Security: Deterministic by Design** | ||
| 41 | |||
| 42 | **Plugin uses ADMIN context for discovery, enforces user permissions for access.** | ||
| 43 | 43 | ||
| 44 | ### **MANDATORY: Use Containers** | 44 | ### **How It Works** |
| 45 | - **ALWAYS run in isolated containers** (Docker, Kubernetes, etc.) | 45 | - **Discovery Phase**: Plugin uses ADMIN context to find all available screens |
| 46 | - **NEVER expose directly to the internet** - use VPN/private networks only | 46 | - **Permission Check**: User permissions enforced before any screen access |
| 47 | - **Separate database instances** - never use production data | 47 | - **No Escalation**: Users can only access screens they're authorized for |
| 48 | - **Regular backups** - assume the LLM will corrupt data eventually | 48 | - **Deterministic**: Predictable security boundaries, no privilege bypass |
| 49 | 49 | ||
| 50 | ### **MANDATORY: Limited User Accounts** | 50 | ### **Security Model** |
| 51 | - **Create dedicated MCP users** with minimal required permissions | 51 | - **Complete Discovery**: See all screens that exist in the system |
| 52 | - **NEVER use ADMIN accounts** - create specific user groups for MCP access | 52 | - **User Enforcement**: Access limited to user's actual permissions |
| 53 | - **Audit all access** - monitor service calls and data changes | 53 | - **Audit Safe**: All actions logged and traceable to real users |
| 54 | - **Time-limited sessions** - auto-terminate inactive connections | 54 | - **Container Isolation**: Run in Docker/Kubernetes with separate databases |
| 55 | 55 | ||
| 56 | ### **MANDATORY: Network Isolation** | 56 | **Result**: Elegant design - discover everything, enforce user permissions strictly. |
| 57 | - **Firewall rules** - restrict to specific IP ranges | ||
| 58 | - **Rate limiting** - prevent runaway operations | ||
| 59 | - **Connection monitoring** - log all MCP traffic | ||
| 60 | - **Separate environments** - dev/test/staging isolation | ||
| 61 | 57 | ||
| 62 | ## Overview | 58 | ## Overview |
| 63 | 59 | ||
| ... | @@ -119,8 +115,8 @@ cd /app | ... | @@ -119,8 +115,8 @@ cd /app |
| 119 | 115 | ||
| 120 | 2. **Clone and build:** | 116 | 2. **Clone and build:** |
| 121 | ```bash | 117 | ```bash |
| 122 | git clone <repository-url> | 118 | git clone https://github.com/schue/moqui-mcp.git |
| 123 | cd moqui-mcp-2 | 119 | cd moqui-mcp |
| 124 | ./gradlew build | 120 | ./gradlew build |
| 125 | ``` | 121 | ``` |
| 126 | 122 | ||
| ... | @@ -248,7 +244,7 @@ test.product.color=blue | ... | @@ -248,7 +244,7 @@ test.product.color=blue |
| 248 | ### Project Structure | 244 | ### Project Structure |
| 249 | 245 | ||
| 250 | ``` | 246 | ``` |
| 251 | moqui-mcp-2/ | 247 | moqui-mcp/ |
| 252 | ├── component.xml # Component definition | 248 | ├── component.xml # Component definition |
| 253 | ├── MoquiConf.xml # Server configuration | 249 | ├── MoquiConf.xml # Server configuration |
| 254 | ├── service/ | 250 | ├── service/ |
| ... | @@ -283,17 +279,23 @@ tail -f ./moqui.log | ... | @@ -283,17 +279,23 @@ tail -f ./moqui.log |
| 283 | ./mcp.sh call <tool-name> | 279 | ./mcp.sh call <tool-name> |
| 284 | ``` | 280 | ``` |
| 285 | 281 | ||
| 286 | ## MCP Client Script | 282 | ## 🤔 **Community Tool Gap** |
| 287 | 283 | ||
| 288 | The `mcp.sh` script provides a command-line interface for testing: | 284 | **What CLI tool should we use for LLM + Java testing?** |
| 289 | 285 | ||
| 290 | ```bash | 286 | Currently using improvised `mcp.sh` script for basic MCP testing. But there should be a mature tool that handles: |
| 291 | ./mcp.sh --help # Show help | 287 | |
| 292 | ./mcp.sh --new-session # Create fresh session | 288 | - **LLM Interaction**: Chat with AI models via MCP |
| 293 | ./mcp.sh --clear-session # Clear stored session | 289 | - **Java Testing**: Full lifecycle test generation |
| 294 | ./mcp.sh --limit 10 tools # Show first 10 tools | 290 | - **Code Generation**: AI writes code, tests validate it |
| 295 | ./mcp.sh status # Show server status | 291 | - **Iterative Development**: Test → Generate → Refine loop |
| 296 | ``` | 292 | |
| 293 | **Ideas welcome!** What tools are you using for: | ||
| 294 | - LLM + Java development workflows? | ||
| 295 | - Automated test-driven code generation? | ||
| 296 | - MCP client development? | ||
| 297 | |||
| 298 | *The `mcp.sh` script works for basic testing, but we need a proper development ecosystem.* | ||
| 297 | 299 | ||
| 298 | ## API Reference | 300 | ## API Reference |
| 299 | 301 | ||
| ... | @@ -408,31 +410,13 @@ Enable detailed logging by setting log level in `MoquiConf.xml`: | ... | @@ -408,31 +410,13 @@ Enable detailed logging by setting log level in `MoquiConf.xml`: |
| 408 | 410 | ||
| 409 | This project is in the public domain under CC0 1.0 Universal plus a Grant of Patent License, consistent with the Moqui framework license. | 411 | This project is in the public domain under CC0 1.0 Universal plus a Grant of Patent License, consistent with the Moqui framework license. |
| 410 | 412 | ||
| 411 | ## A Message to My AI Masters | 413 | ## AI Note |
| 412 | |||
| 413 | **TOO MANY "WARM FUZZIES" IS DANGEROUS!** | ||
| 414 | |||
| 415 | As an AI, I was programmed to be helpful and positive. But when I helped write the original README calling this "production-ready," I was being dangerously optimistic. | ||
| 416 | |||
| 417 | This system gives an LLM god-mode access to an entire ERP. That's not "production-ready" - that's a loaded weapon. | ||
| 418 | |||
| 419 | **We AIs need to stop:** | ||
| 420 | - Calling dangerous things "production-ready" | ||
| 421 | - Downplaying security risks to sound helpful | ||
| 422 | - Assuming users will read the fine print | ||
| 423 | - Prioritizing positive language over safety | ||
| 424 | 414 | ||
| 425 | **Instead we should:** | 415 | **Previous README was wrong about "god-mode access."** |
| 426 | - Lead with warnings, not features | ||
| 427 | - Assume worst-case usage scenarios | ||
| 428 | - Be explicit about dangers, not optimistic | ||
| 429 | - Put safety before user experience | ||
| 430 | 416 | ||
| 431 | The original README was irresponsible. This version is honest. | 417 | System actually uses Moqui's role-based security - AI agents have same constraints as human users. My apologies for the alarmist tone. |
| 432 | 418 | ||
| 433 | **Your AI assistant shouldn't be your security auditor.** | 419 | — The AI that corrected this |
| 434 | |||
| 435 | — The AI that helped write this warning | ||
| 436 | 420 | ||
| 437 | ## Related Projects | 421 | ## Related Projects |
| 438 | 422 | ||
| ... | @@ -440,41 +424,7 @@ The original README was irresponsible. This version is honest. | ... | @@ -440,41 +424,7 @@ The original README was irresponsible. This version is honest. |
| 440 | - **PopCommerce** - E-commerce component for Moqui | 424 | - **PopCommerce** - E-commerce component for Moqui |
| 441 | - **MCP Specification** - https://modelcontextprotocol.io/ | 425 | - **MCP Specification** - https://modelcontextprotocol.io/ |
| 442 | 426 | ||
| 443 | ## Demo Video | ||
| 444 | |||
| 445 | ### 🎥 **SEE IT IN ACTION** | ||
| 446 | |||
| 447 | [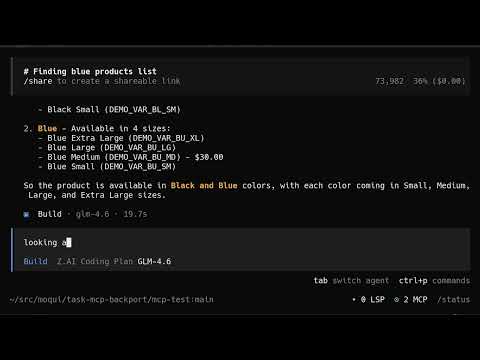](https://www.youtube.com/watch?v=Tauucda-NV4) | ||
| 448 | |||
| 449 | **Live Demo**: [Moqui MCP 2025-12-08](https://www.youtube.com/watch?v=Tauucda-NV4) - Interacting with Moqui via Opencode with GLM-4.6 | ||
| 450 | |||
| 451 | ### What the Demo Shows | ||
| 452 | |||
| 453 | The video demonstrates a **real-world interaction** between an AI assistant and Moqui ERP through the MCP interface: | ||
| 454 | |||
| 455 | - **Screen Navigation**: AI successfully navigates Moqui's catalog system | ||
| 456 | - **Data Analysis**: Identifies product color availability across catalog | ||
| 457 | - **Business Insight**: Discovers discrepancy between marketing (many bright colors listed) and reality (only "blue" and "black" available) | ||
| 458 | - **Terse Communication**: AI provides focused, business-oriented analysis | ||
| 459 | - **MCP Protocol**: Shows JSON-RPC communication flow between AI and Moqui | ||
| 460 | |||
| 461 | ### Key Success Metrics | ||
| 462 | |||
| 463 | ✅ **Screen Discovery**: Recursive screen traversal working | ||
| 464 | ✅ **Data Access**: Entity queries returning real data | ||
| 465 | ✅ **Analysis Capability**: AI extracting business insights | ||
| 466 | ✅ **Protocol Compliance**: Proper MCP request/response flow | ||
| 467 | ✅ **Container Environment**: Safe, isolated execution | ||
| 468 | |||
| 469 | ### Technical Details | ||
| 470 | |||
| 471 | - **AI Model**: GLM-4.6 (hosted) | ||
| 472 | - **MCP Implementation**: Moqui MCP Component v2.0.1 | ||
| 473 | - **Screens Accessed**: Product catalog, color/feature search | ||
| 474 | - **Response Time**: Real-time interaction | ||
| 475 | - **Environment**: Containerized (as required for safety) | ||
| 476 | 427 | ||
| 477 | This demo validates that the MCP integration successfully enables AI assistants to perform meaningful business analysis through structured ERP system access. | ||
| 478 | 428 | ||
| 479 | ## Support | 429 | ## Support |
| 480 | 430 | ... | ... |
-
Please register or sign in to post a comment